Email Productivity Module
Abnormal Security protects its enterprise customers from email attacks with machine learning and natural language processing. We built graymail functionalities to address some of the security teams’ concerns but needed a way to convey its value, so I designed a dashboard that repositioned the product and enabled its success.
Due to confidentiality agreement, I generalized the content.
Context: Abnormal was working closely with our customers’ security teams to understand how the company can move from tackling one specific malicious emails (as an security security add-on product) to protecting all our customers’ emails (as a full email security product).
Problem: Based on user interviews (a dozen discovery calls, in addition to 3-5 design partners syncs per week), we learned many users want more…
Control and flexibility: Instead of letting all non-malicious emails go through the normal emails flow, many users asked if we can let them choose where spam (unwanted and unsolicited emails), graymail (bulk emails that are often wanted), and suspicious emails land.
Visibility: In addition to seeing the malicious emails, our users want more visibility of what Abnormal determines as spam, graymail, and suspicious emails.
Protection: Some established email security services send suspicious emails into a separate folder for end-users (employees) to review, as a “daily digest.” Security team asked if we can offer a similar feature to expand our protection beyond screening for malicious emails.
Background: We explored several solutions, but for various reasons, they did not stick:
Providing policy management functionalities to improve flexibility — I created policy management mockups that were well-received by our design partners. However, after careful consideration, leadership team decided not to fully pursue this solution, because customers loved Abnormal Security for the “simplicity” of the solution. Moving into policy management deviated from our market position of a policy-free solution that reduces operation cost.
Showing all spam and graymail to increase visibility — Our beta-testing customers loved the visibility, however, we pivoted away because of storing large volume of graymails would result in significant infrastructure cost and potential security concern.
Providing a graymail management product to expand protection — We built the functionality to triage graymail and allow end-users’ feedback to improve our model. For example, Abnormal Security automatically places a vendor newsletter into a Promotions folder. If the user drags the email back to Inbox, the next newsletter from this vendor will automatically land in the Inbox. This provides a superior email viewing experience than getting daily digest — where employees can control what safe email or graymail go into the Promotions folder and they do not need to wait for daily digest to see legitimate vendor emails.
Although it was a good product, it was difficult to sell this feature to security teams, as an add-on to our core email protection services.
As part of the explorations, we interviewed Chief Security Officers, and learned some of them care deeply about employee productivities. Instead of focusing on security alone, we decided to tackle all the aforementioned problems and to highlight the value of our graymail engine from a productivity angle.
Case Study: How we designed and launched a successful productivity dashboard within 30 days.
My Role: I was the sole designer on this project, while juggling several projects and transitioning into Design team management. I collaborated with cross-functional partners to:
Determine what to show in the dashboard
Guide team with productivity calculation
Create prototypes and pitch to the leadership team
Ensure successful product delivery
Visualize and sequence enhancements, plan subsequent iterations
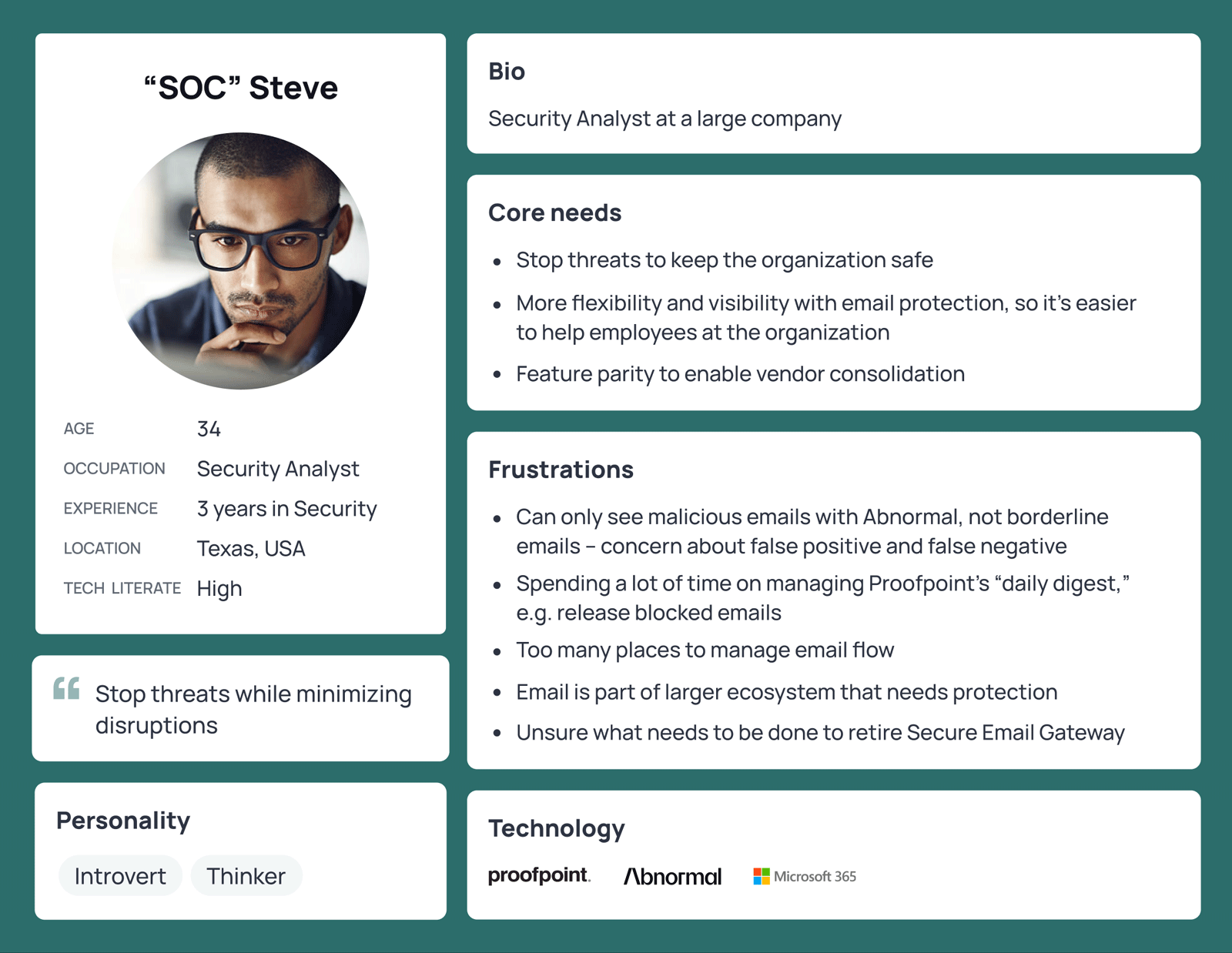
Persona: For this project, I outlined two persona for team alignment:
Cam, the Chief Security Officer — Economic buyer
Steve, the Security Analyst — User of the Abnormal portal
Both Cam and Steve are also “end-users” of our email protection and the graymail management module.

Research: Although my usual design process at Abnormal involved initial user research, design in collaboration with Product Manager and Engineers, usability testing, and revision; I tried a different approach for this project, because we had a tight deadline:
I sent out an informal survey to 10 subject matter experts within the company to understand what they think are our customer’s top needs relating to spam, graymail, and productivity metrics. The list of individuals ranged from Sales Engineers, Customer Success Managers, Solution Architects, to Product Managers, the Business Value Generation team, and Data Scientists.
I searched and analyzed existing customer interview data for information relevant to dashboard, graymail, spam, and productivity.
I then drafted and ranked a list of top metrics we want to monitor, and met with our Lead Engineer and Product Manager to determine what are feasible for the initial launch. My quick research approach enabled the team to identify what our customers wanted and what we can build, all within a day.
I created an initial dashboard mockup including the highest value metrics that we can ship within the time frame, and sent them back to my survey recipients for additional feedback.
Wireframes: The wireframe evolved throughout the rest of the week, as we met with leadership for feedback and guidance. We iterated to put more emphasis in the productivity calculations.
We want to estimate time saved for customers’ employees when we triage graymail to a different location. The team proposed one formula (#2 below), which I suspected to be overly conservative. To ensure the dashboard shows meaningful data, I reached out to a data scientist to get a simulation based on our initial productivity saving formula. Based on the simulations, I suggested adjustments to our productivity (#3 below), which 4x the “productivity savings” calculation and was the formula we launched in our release:
Then I finalized the design and created mockups to cover other scenarios, such as trials, partial adoption, full adoption, and potential errors.
Reception:
This product was well received by our customers.
As the Head of Security of one of our customers put it, “I receive hundreds of promotional emails. If I were to go through them all, it would probably take up to 30% of my time each day. The Email Productivity module allows our users to focus on more important business projects to meet our goals.”
The Chief Information Security Officer of another large company said, “We get so much graymail in this environment. Abnormal has already paid for itself just by increasing employee productivity.”
It accounted for 10% of our Annual Recurring Revenue within first month of launch and became part of our long-term product offering.
Preparing for the future:
Creating a dashboard allowed us to officially launch the Email Productivity Module, which helps to protect our customers spam and graymail. This also opens the door to address our users’ concerns in visibility and flexibility. While the team was developing the dashboard, I mocked up additional features that enabled quick and fruitful follow-up customer conversations. The mockup areas included:
Increase visibility: Allow analysts to search for spam messages, in case retrieval and removal were necessary. This search first approach will not require email storage in our system, therefore limiting infrastructure cost. The search will also be audited and limited to specific roles, adhering to our security standards.
Give our users control and flexibility: Allow some emails to bypass the productivity filter, but still be scanned for malicious content
Bypass based on sender, e.g. company’s voicemail transcription service
Bypass based on recipients to align with their preferences
Getting users’ feedback and showing mockups that address their concerns allowed customers to see us as nimble and invested.
Learnings:
Successful products are not only well designed and implemented, but also marketable and maintainable. Our earlier attempts to solve user problems were unsuccessful because we focused on addressing our immediate users’ pain points, without careful consideration of marketability and operational costs. Successful product designs find the intersection of business needs, user needs, and engineering feasibility (given the time constraints).
Consider all key persona. When the economic buyer and the user of the products are not the same, it’s important to design for both.
Internal research can be a reasonable proxy for customer input, when the surveyed individuals have deep understanding of customers’ needs in the area of focus.
The usefulness of a dashboard is highly dependent on its data. When committing to a dashboard design, check the numbers and formula by running simulations or sampling data.






